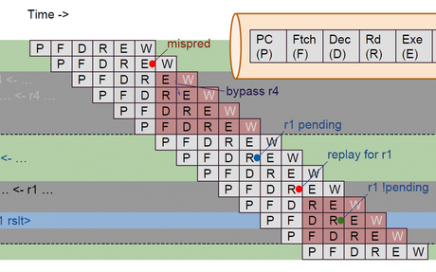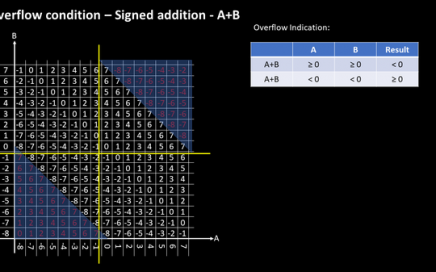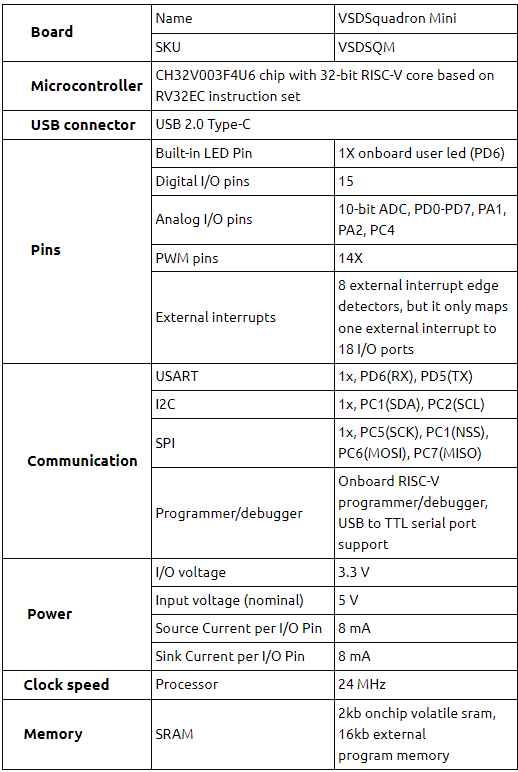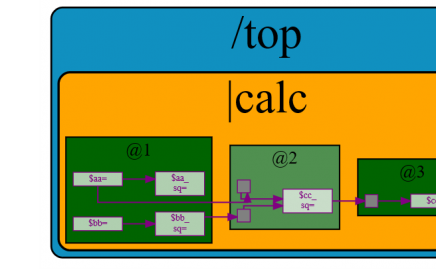
Symposium I – Front-end open-source EDA tool flows for IC design and verification
Question – Who doesn’t want a 3.5X improvement in their code size? I guess everyone wants efficient and effective improvement. Now these are just few tips to have the easy implementation of pipe-line. You are free to implement your ideas in TL-verilog, compile, simulate and see the improvements on your own. For few more tips, you might want to check out below course on “VSD – Pipelining RISC-
V with TL-verilog”